5 The Base product (Windows)
5.1 HELIOS architecture on Windows
HELIOS Base is the foundation for all HELIOS products and contains all basic libraries, the HELIOS Admin administration software, and additional powerful tools.
5.1.1 Optimal integration into Windows
Windows Services are administered by the HELIOS Service Controller
Windows shares can be published as HELIOS volumes
HELIOS supports Windows ACL (Access Control List) permissions
Windows users/groups (local and AD/PDC) are supported by HELIOS
Windows file changes are reported to the HELIOS notification server via the HELIOS file event driver
System messages, issued by HELIOS services, are written to the Windows event log (see 5.3 “Windows event log”)
Windows Unicode is used by HELIOS
Windows print jobs can be automatically forwarded to HELIOS printer queues (see 15.9.1 “Connect the Windows printing system with HELIOS queues”)
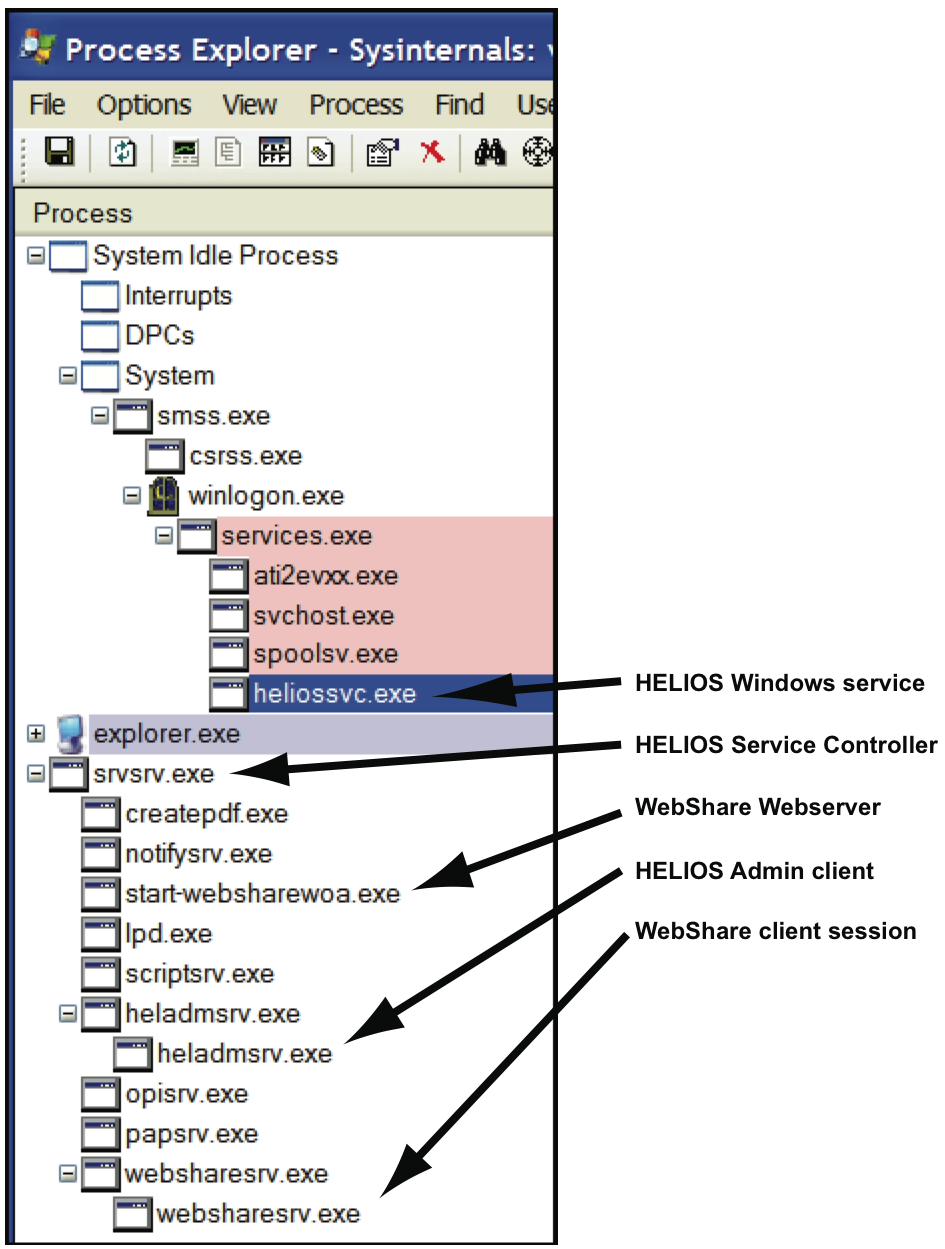
5.1.2 HELIOS server processes on Windows
All processes are monitored and administered by the HELIOS Service Controller. One master process is started for each service, additional client processes are spawned for each user/session. The security is enforced by each session running as an authenticated user. There are various options for process auditing and tracing.
5.1.3 Starting and stopping the HELIOS software
The HELIOS services are started automatically when Windows is booted. This is done by the HELIOS Windows service “heliossvc”.
The HELIOS services can be started or stopped manually by any user with administrative rights (i.e. member of the “Administrators” group).
The “start-helios” command (in “HELIOSDIR\bin”) starts the HELIOS Windows service “heliossvc” which runs with system privileges and calls “start-helios -a” to actually start the HELIOS services. This is done to ensure that all HELIOS services are running with system privileges, regardless of who called “start-helios”.
Likewise, “stop-helios” causes the HELIOS Windows
service “heliossvc” to call stop-helios -a
with system privileges.
The Windows Services tool (Administrative Tools >
Services) allows you to start and stop HELIOS services in
the Windows GUI.
- Note:
-
Neither “start-helios” nor “stop-helios” can print messages of starting/stopping HELIOS services to the console. If an error occurs, both services issue a generic message and refer to the Windows event log (see 5.3 “Windows event log”).
5.2 Windows permissions
Windows SIDs (Security Identification) are used almost everywhere in Windows. They are very complex and include machine information, domain information, user/group information, etc. Each user or group has a unique SID. A typical user SID has a length of 224 bit.
The HELIOS “authutil” program maps the Windows SIDs into 32-bit IDs and back, in order to be used with “htar”, “dt tools”, printing, accounting, etc.
The “authutil” login command shows the effective permissions, including the mapped HELIOS user ID of the Windows SID and the HELIOS group IDs (see 10.2 “authutil”).
- Example:
$ authutil login -n Administrator -p secret -s user: Administrator uid: 67109364 <S-1-5-21-527237240-2111687655-1343024091-500> gid: 67109377:None long name: <null> last refresh: Thu Aug 27 09:32:12 2009 origin: Windows <*> homedir: <null> admin: system,queue,printer,WebShare groups: None:67109377, Everyone:16842752, Administrators:0, User s:35652129, INTERACTIVE:17104900, Authenticated Users:17104907, LOCAL: 16908288 This organization:17104911, NTLM Authentication:37748746 This organization:17104911, NTLM Authentication:37748746
“authutil” also delivers information on a certain user without logging in, via the user name (Example 1) or the mapped HELIOS user ID (Example 2):
- Example 1:
$ authutil user -n Administrator user: Administrator uid: 67109364 <S-1-5-21-527237240-2111687655-1343024091-500> gid: -1:<null> long name: <null> last refresh: Thu Aug 27 09:35:31 2009 origin: Windows <*> homedir: <null> groups: Administrators:0
- Example 2:
$ authutil user -i 67109364 user: Administrator uid: 67109364 <S-1-5-21-527237240-2111687655-1343024091-500> gid: -1:<null> long name: <null> last refresh: Thu Aug 27 09:37:04 2009 origin: Windows <*> homedir: <null> groups: Administrators:0
Windows ACLs specify SID access lists for files, services and resources. They differ from UNIX ACLs, and also from TCP/IP ACLs.
5.2.1 Permissions for owner and group
On UNIX, access rights and permissions can be set via the HELIOS tools “dt chown” and “dt chmod”. In the following example, the file “file” is set to allow owner and group read/write permissions, and others read-only. The HELIOS tools “dt chown” and “dt chmod” are described in 8.11.1 “Command descriptions”.
- Example:
# dt chown mike:helios file # dt chmod 664 file
A directory listing shows the effect of the action:
# dt ls -l file ... -rw-rw-r-- 1 mike helios 160 Mar 15 2005 file ...
On Windows, ACLs specify file permissions for the owner, the group and others.
HELIOS file access is always performed using the Windows file system. Hence, all Windows file permissions and ACLs are always honored.
The Windows program “icacls” allows displaying or modifying ACLs. “icacls” is documented by Microsoft.
- Note:
-
The HELIOS tools “dt chown”, “dt chgrp” and “dt chmod” can map UNIX permissions to Windows ACLs. This allows setting the same permissions, using the same syntax across platforms (Windows, Mac, UNIX), for the convenience of users and administrators. We recommend to set owner, group and permissions with these “dt” tools.
5.3 Windows event log
Messages issued by HELIOS services are stored in the “Application” event log file which is accessible via the Windows “Event Viewer” (Administrative Tools > Event Viewer).
The HELIOS logs can also be accessed via the HELIOS
Admin System Messages list or by use of the HELIOS
“psyslog” utility. Unlike the Windows “Event Viewer”,
“psyslog“ (see 8.24 “psyslog”) need not be refreshed
manually and can be used in batch mode.
5.4 File name encoding
There are different methods of file name encoding. For example, we assume the file name “Müller”.
This encoding method is used by many client applications including “cmd.exe”, “perl.exe”, “ZIP”, etc. The file name “Müller” in the PC850 encoding is:
4d 81 6c 6c 65 72
Unicode can contain different encodings. The file name “Müller” in the Windows UCS16 encoding is:
00 4d 00 fc 00 6c 00 6c 00 65 00 72
The file name “Müller” in UTF-8 encoding (which is used by HELIOS) is:
4d c3 bc 6c 6c 65 72
- Note:
-
HELIOS “dt” tools or ImageServer file events use the UTF-8 encoding.
The HELIOS “uniconv” tool converts between different encodings (see 8.5 “uniconv”).
5.5 HELIOS CLI parameters
The HELIOS CLI (Command Line Interface) tools accept Unicode input parameters. Internally HELIOS uses UTF-8.
- Note:
-
Perl only supports 8-bit Windows encoding. This is important to know since HELIOS scripts, e.g. WebShare scripts, are based on Perl. By default, Windows uses the PC-850 character set and converts parameters from/to PC-850.
HELIOS CLI tools support simple Windows wildcard parameters:
* = None, one, or more characters ? = single character
Windows command arguments containing spaces must be called quoted, e.g.:
"\Program Files\HELIOS\bin\dt.exe" ls -l "C:\My Files\Docs\"
To verify the parameters that are passed to programs, the
HELIOS “uniconv” tool (8.5 “uniconv”) supports the -e
option to echo all arguments.
- Example:
$ uniconv -e 123 Hello World "Hello HELIOS"
will print:
ARGV[0]: uniconv ARGV[1]: -e ARGV[2]: 123 ARGV[3]: Hello ARGV[4]: World ARGV[5]: Hello HELIOS
5.6 File path information
UNIX file paths are delimited by slashes (“/”), e.g.:
/data1/myfiles/filename
Windows file paths are delimited by backslashes (“\”), e.g.:
C:\data1\myfiles\filename
HELIOS uses a normalized path syntax. This allows referencing
files on Windows or on UNIX in case Windows data is restored in UNIX, e.g.:
/C:/data1/myfiles/filename (standard HELIOS file path).
Windows file paths are also supported by HELIOS, e.g.:
C:\data1\myfiles\filename C:/data1/myfiles/filename
HELIOS supports Windows reparse points similarly to
UNIX mounts, e.g.:
“disk 1 partition 5” is mounted as C:\data.
Although HELIOS supports Windows hard links, it is advised to use them with caution. Support is provided using the HELIOS “ln” tool (see 8.28.2 “ln”).
In Windows there is no feature similar to UNIX symbolic links.
Within HELIOS applications emulated symlinks do work.
The HELIOS command ln -s allows creating symlinks.
On the Windows NTFS (NT File System), each file or
directory is assigned a unique 64-bit-based ID number. This is similar
to the Apple HFS/AFP ID number for files and directories.
In addition, Windows assigns a unique volume identifier
ID. The unique IDs on Windows and UNIX can be viewed
via the dt ls -i command.
- Example:
$ dt ls -i "\Program Files\helios\Public" 2814749767188534 Documentation 2533274790477893 Java 5066549580873721 MacOS 38280596832731537 WebShare 2251799813767233 Windows
You may additionally specify the -l option (“long”) along
with the -i option in order to get the extended output.
5.7 Windows shares & HELIOS volumes
Windows shares are folders that can be accessed in a
network by other computers. They are managed by Windows Explorer, or
with the “Computer Management” tool.
Windows shares are automatically listed in the HELIOS Admin
Volumes tab and displayed in the SMB name column,
so that HELIOS settings (e.g. OPI layouts) can be customized with HELIOS
Admin. It is not possible to delete such a volume from within HELIOS Admin.
You need to turn off Windows sharing of that directory from within
Explorer or “Computer Management”.
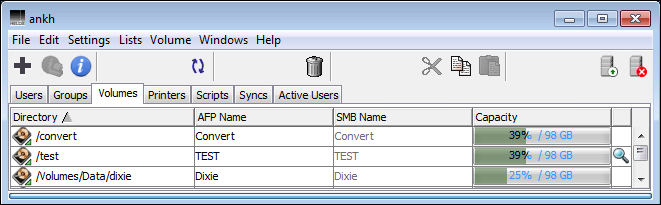
Grayed-out volumes in the HELIOS Admin volume list indicate that the volume is defined as a HELIOS volume, but is not defined as a Windows share (see the “Convert” volume in Fig. 5.1).
5.8 Modifications in the Windows system
5.8.1 DLL search path for HELIOS libraries
All HELIOS tools and services require several HELIOS libraries that are installed in “HELIOSDIR\lib”. HELIOS Installer adds this path to the Windows search path, so that HELIOS programs will find the libraries.
- Note:
-
Sometimes third-party installers or users modify the Windows search path, which may result in missing library error messages. Issuing a
stop-heliosandstart-helios -iwill fix this.
5.8.2 HELIOS files copied into the Windows folder
If a USB dongle is used for providing the machine ID (see What you have to do in “Welcome to HELIOS Base”), its driver files are copied into the “WINDOWS\system32\drivers” and the “WINDOWS\inf” directory. This is done by Windows during the driver installation.
The HELIOS print monitor driver “HELIOSPrinterMon64_s.dll” is copied from “HELIOSDIR\etc\printmon” into the “WINDOWS\system32” folder.
5.8.3 Windows registry entries
When the HELIOS software is installed on the Windows platform, only a few changes are applied to the Windows registry in “HKEY_LOCAL_MACHINE”.
Uninstall info:
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HELIOS
HELIOS installation path:
SOFTWARE\HELIOS Software GmbH\Helios
Event log:
SYSTEM\CurrentControlSet\Services\Eventlog\Application\Helios SYSTEM \CurrentControlSet\Services\Eventlog\Application\heliossvc
Environment:
SYSTEM\CurrentControlSet\Control\Session Manager\Environment
- Note:
-
All other settings for the HELIOS modules are stored in the HELIOS Preferences and configuration files.
5.9 HELIOS file event driver
The HELIOS file event driver is a kernel driver that monitors the HELIOS volumes and reports file changes to the HELIOS notification server. This is needed e.g. for the ImageServer product to generate layout files or to trigger hot folder actions.
The driver (“HELIOS_FileEvent64.sys”), is located in “HELIOSDIR\etc\kernel”. The notification server “notifysrv” loads the file event driver when it is started. The driver remains loaded until Windows is shut down.
If an update for the file event driver should become available, Windows must be rebooted to load the updated driver. Otherwise “notifysrv” will issue the following error message at startup:
A previous version of the kernel driver is already loaded. You must reboot the computer to load the updated kernel driver.
In the case of a Windows crash within 2 minutes after “start-helios”, the file event driver is not loaded with the next “start-helios”. In this case, “notifysrv” will issue the following error message at startup:
Kernel driver not loaded because the file "HELIOSDIR/var/run/kdrvStart" exists. This could be caused by an abnormal termination of the notify server. You must delete this file and restart the HELIOS services to get the driver loaded again.
The HELIOS services will start, but no file events will be reported to the notification server and therefore automatic layout generation or hot folder actions in ImageServer will not work. The file event driver will not be loaded until you delete the file “HELIOSDIR\var\run\kdrvStart” and restart the HELIOS software.
Third-party applications can use the “Notification feature” of ImageServer to receive information about file and directory changes in HELIOS volumes.
5.10 Windows firewall problems
All installed firewalls must be turned off for the initial HELIOS installation. After a successful HELIOS software installation, all services without firewall, anti-virus software, etc. must be tested.
If everything works as expected, the HELIOS services should be tested again, with enabled firewall. The ports that the services use are listed in chapter C.8 “TCP ports used by HELIOS”.
- Note:
-
Some firewalls will not allow localhost TCP/IP communications needed by HELIOS. Also, many problems can occur with firewall configurations that do not allow HELIOS TCP/IP communications. Custom firewall configuration is needed in this case.
The command socket -v <servername> <port> can be used to
investigate on firewall related issues.
The HELIOS “socket” program is described in
8.6 “socket”.
5.11 HELIOS Admin notes
On Windows, HELIOS Admin provides less administration, compared to its UNIX counterpart. This is because Windows file services and authentication methods are used instead of the corresponding HELIOS services (see Available products in 4.1.9 “Software installation (Windows)”:
No
Security SettingsmenuNo
Syncstab in the main window. The related HELIOS “dt sync” tool is not available on Windows.No
Windows,WINSandDHCPtabs in theServer SettingsmenuNo
Starting Program,User Home Directory,Primary Group,
Minimum User/Group IDin theGeneraltab of theServer Settingsmenu
HELIOS Admin cannot be used to administer Windows users or groups. They can be viewed as a read-only list.
HELIOS Admin administrative groups are not created during the installation. The groups “SysAdm”, “PrnAdm”, “WSAdm” and “QueueAdm” should be created via Windows to allow control of administrative rights within HELIOS modules. Refer to Security – who can use HELIOS Admin? for full details.
- Note:
-
Under Windows, any member of the “Administrators” group is functionally equivalent to the user “root” under UNIX. Hence, a member of the “Administrators” group can log on to HELIOS Admin and receive full administrative rights.
Under Windows, HELIOS Base does not contain the HELIOS authentication server (“authsrv”). Authentication is automatically configured to use local users and AD/PDC users. However, the “authutil” tool is available as described in 5.2 “Windows permissions”.
5.12 “srvmsg” program notes
On Windows installations, the HELIOS program “srvmsg” behaves slightly different than its counterpart on UNIX:
When calling “srvmsg” with the -d and -D
options for auditing purposes, only the specified process is
traced. Forked child processes are not automatically traced in
the live auditing. They must be called with their own spawned
process ID.
The usage and all available options of the “srvmsg” program is described in chapter 8.1 “srvmsg”.
5.13 PAP and HELIOS TCP Printing
For printing from a Mac client to the HELIOS printing system, HELIOS provides the Mac PAP and HELIOS TCP printers.
For better performance, print queues can be published as HELIOS TCP printers. For this the “HELIOS TCP” printer driver must be installed on each Mac client. The following table gives an overview on the required plug-in that has to be installed for configuring the HELIOS TCP printer.
| Client | HELIOS TCP Printer plug-in |
| OS X | HELIOSTCPPrinter.dmg |
| Mac OS 9 | HELIOS TCP Chooser/HELIOS TCP Printer |
Installing and configuring HELIOS TCP printers is described in the chapters “Printer spooler settings”, “PAP printer output settings” and “HELIOS TCP Printer driver” in the HELIOS EtherShare manual.